78 lines
2.8 KiB
Markdown
78 lines
2.8 KiB
Markdown
[](https://app.codacy.com/app/jollheef/out-of-tree?utm_source=github.com&utm_medium=referral&utm_content=jollheef/out-of-tree&utm_campaign=Badge_Grade_Dashboard)
|
|
[](https://goreportcard.com/report/code.dumpstack.io/tools/out-of-tree)
|
|
[](https://out-of-tree.readthedocs.io/en/latest/?badge=latest)
|
|
[](https://www.paypal.com/cgi-bin/webscr?cmd=_s-xclick&hosted_button_id=R8W2UQPZ5X5JE&source=url)
|
|
[](https://blockchair.com/bitcoin/address/bc1q23fyuq7kmngrgqgp6yq9hk8a5q460f39m8nv87)
|
|
|
|
# [out-of-tree](https://out-of-tree.io)
|
|
|
|
out-of-tree kernel {module, exploit} development tool
|
|
|
|
out-of-tree is for automating some routine actions for creating development environments for debugging kernel modules and exploits, generating reliability statistics for exploits, and also provides the ability to easily integrate into CI (Continuous Integration).
|
|
|
|
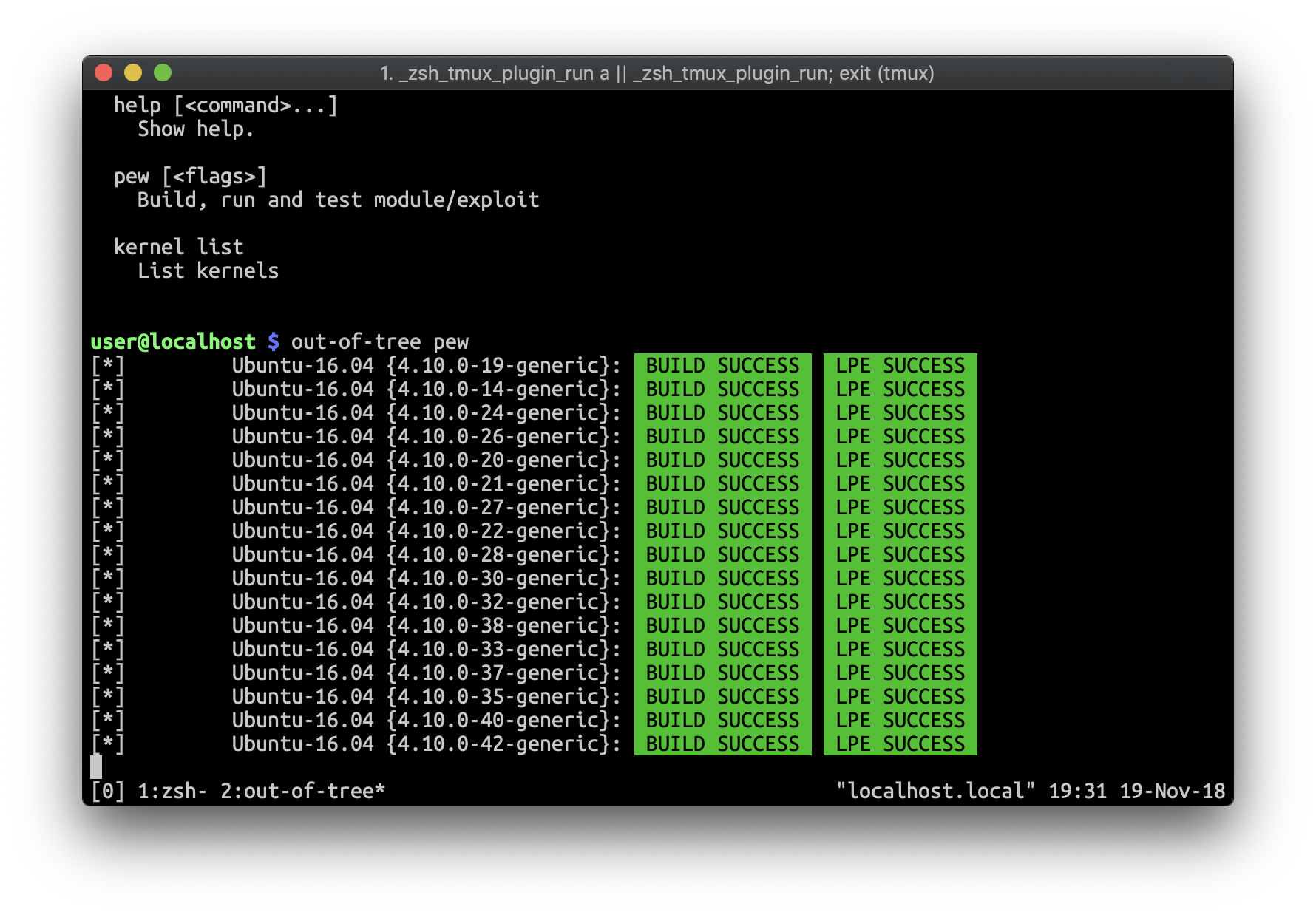
|
|
|
|
## Installation
|
|
|
|
### GNU/Linux (with [Nix](https://nixos.org/nix/))
|
|
|
|
$ curl -fsSL https://get.docker.com | sh
|
|
$ sudo usermod -aG docker user && newgrp docker
|
|
$ curl -L https://nixos.org/nix/install | sh
|
|
$ nix-env -iA nixpkgs.out-of-tree
|
|
|
|
Note that adding a user to group *docker* has serious security implications. Check Docker documentation for more information.
|
|
|
|
### macOS
|
|
|
|
$ brew cask install docker
|
|
$ open --background -a Docker && sleep 1m
|
|
$ brew tap jollheef/repo
|
|
$ brew install out-of-tree
|
|
|
|
Read [documentation](https://out-of-tree.readthedocs.io) for further info.
|
|
|
|
## Examples
|
|
|
|
Run by absolute path
|
|
|
|
$ out-of-tree --path /path/to/exploit/directory pew
|
|
|
|
Test only with one kernel:
|
|
|
|
$ out-of-tree pew --kernel='Ubuntu:5.4.0-29-generic
|
|
|
|
Run debug environment:
|
|
|
|
$ out-of-tree debug --kernel='Ubuntu:5.4.0-29-generic
|
|
|
|
Test binary module/exploit with implicit defined test ($BINARY_test)
|
|
|
|
$ out-of-tree pew --binary /path/to/exploit
|
|
|
|
Test binary module/exploit with explicit defined test
|
|
|
|
$ out-of-tree pew --binary /path/to/exploit --test /path/to/exploit_test
|
|
|
|
Guess work kernels:
|
|
|
|
$ out-of-tree pew --guess
|
|
|
|
Use custom kernels config
|
|
|
|
$ out-of-tree --kernels /path/to/kernels.toml pew
|
|
|
|
Generate all kernels
|
|
|
|
$ out-of-tree kernel genall --distro Ubuntu --ver 20.04
|
|
|
|
## Troubleshooting
|
|
|
|
If anything happens that you cannot solve -- just remove `$HOME/.out-of-tree`.
|
|
|
|
But it'll be better if you'll write the bug report.
|
|
|
|
## Development
|
|
|
|
Read [Qemu API](qemu/README.md).
|