43d42c2242419ab4c651739d0f76d040b1190848
Nix application VMs: security through virtualization
Simple application VMs (hypervisor-based sandbox) based on Nix package manager.
Uses one read-only /nix directory for all appvms. So creating a new appvm (but not first) is just about one minute.
Dependencies
$ sudo apt install golang virt-manager curl git
$ sudo usermod -a -G libvirt $USER
$ echo 'export GOPATH=$HOME/go' >> ~/.bash_profile
$ echo 'export PATH=$PATH:$GOPATH/bin' >> ~/.bash_profile
$ echo 'source ~/.bash_profile' >> ~/.bashrc
$ source ~/.bash_profile
You need to relogin if you install virt-manager (libvirt) first time.
Install Nix package manager
$ sudo mkdir -m 0755 /nix && sudo chown $USER /nix
$ curl https://nixos.org/nix/install | sh
$ . ~/.nix-profile/etc/profile.d/nix.sh
Libvirt from user (required if you need access to shared files)
$ echo user = "\"$USER\"" | sudo tee -a /etc/libvirt/qemu.conf
$ sudo systemctl restart libvirtd
Install appvm tool
$ go get code.dumpstack.io/tools/appvm
Update appvm tool
$ go get -u code.dumpstack.io/tools/appvm
Generate new application
$ nix-channel --list
nix https://nixos.org/channels/nixos-unstable
$ appvm generate nix.firefox
Run application
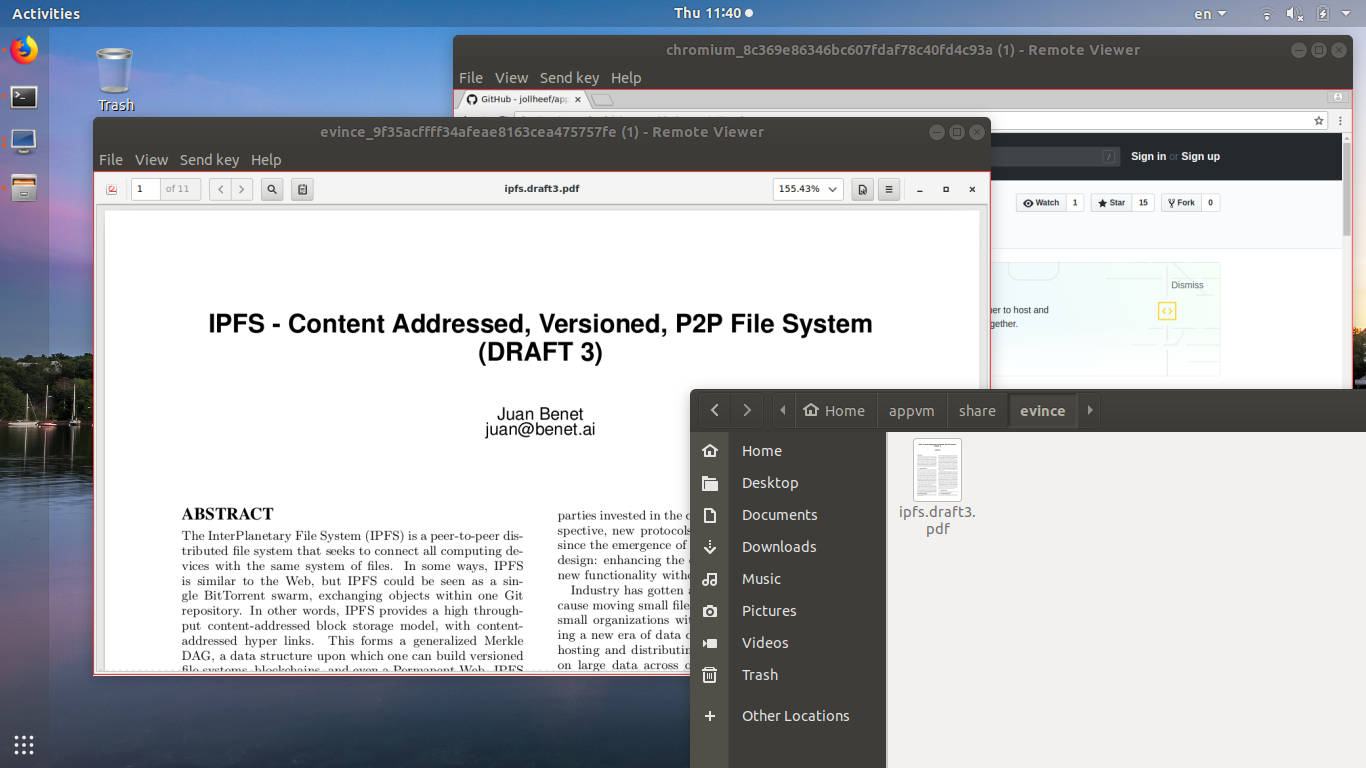
$ appvm start chromium --verbose
$ # ... long wait for first time, because we need to collect a lot of packages
You can customize local settings in ~/.config/appvm/nix/local.nix.
Default hotkey to release cursor: ctrl+alt.
Shared directory
$ ls appvm/chromium
foo.tar.gz
bar.tar.gz
Close VM
$ appvm stop chromium
Automatic ballooning
Add this command:
$ appvm autoballoon
to crontab like that:
$ crontab -l
* * * * * /home/user/dev/go/bin/appvm autoballoon
App description
$ cat nix/chromium.nix
{pkgs, ...}:
{
imports = [
<nixpkgs/nixos/modules/virtualisation/qemu-vm.nix>
<nix/base.nix>
];
services.xserver.displayManager.sessionCommands =
"while [ 1 ]; do ${pkgs.chromium}/bin/chromium; done &";
}
For create new app you should add package name (search at https://nixos.org/nixos/packages.html) and path to binary (typically same as package name).
Description
Languages
Go
84.6%
Nix
13.2%
Makefile
2.2%